With only limited trial fundings, I like to try and combine as much learning as I can into a single project as I can. Since the AWS acquisition, I have been anxious to try the CloudEndure migration solution out hands on.
My goal was to setup a SharePoint 2019 w/ SQL Server 2016 backend environment inside of GCP and migrate this to AWS. Why GCP? Just for learnings sake. I’ve done very little with GCP to this point and all knowledge is good. I figured if you can migrate SharePoint and SQL Server (at least on the Microsoft Windows side) then you can migrate most anything.

In an earlier post (AWS to Azure Connectivity) I demonstrated how you configure a site-to-site VPN connection between Azure and AWS. Only slightly different is the process to connect GCP and AWS. You can basically follow this guide:
https://cloud.google.com/files/CloudVPNGuide-UsingCloudVPNwithAmazonWebServices.pdf
Be sure to set your GCP project network tier as “Standard” rather than “Premium” at least for this example.
With network connectivity established between AWS and GCP, I setup a very basic SharePoint 2019 environment inside of GCP with the actual domain services running in AWS. There were a few things I had to learn about GCP including:
- Basic networking setup.
- Basic VPN configuration to connect GCP to AWS.
- Cloud NAT configuration for instances to access the internet.
- Basic firewall rules to allow communications between instances in GCP and from the AWS VPC.
At this point I had a working SharePoint 2019 environment that I have decided to migrate to AWS.
Step 1: Setup CloudEndure Account
Setup your CloudEndure account at www.cloudendure.com The account setup is fairly straightforward.
Step 2: Setup AWS Credentials
From AWS setup the necessary IAM user and permissions as defined in this IAM policy statement: CloudEndure Policy You will need the AWS access key / secret key to plug into your CloudEndure project.
Step 3: Create the CloudEndure Project
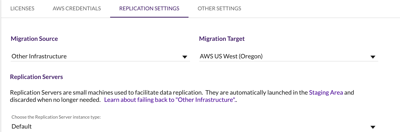
For the replication settings we will choose one of the private subnets in our AWS environment.
Step 4: Install the CloudEndure Agent
We can now install the CloudEndure agent on our target machines (sp2019, spsql1) from: https://console.cloudendure.com/installer_win.exe
C:\installer_win.exe -t <token> –no-prompt
The installation of the CloudEndure Agent has started.
Connecting to CloudEndure Console… Finished.
Checking the disk free space.
Identifying disks for replication.
Disk to replicate identified: d:0 of size 100.0 GiB
Disk to replicate identified: c:0 of size 50.0 GiB
All disks for replication were successfully identified.
Downloading CloudEndure Agent… Finished.
Installing CloudEndure Agent… Finished.
Adding the Source machine to CloudEndure Console… Finished.
Instance ID: 7292093570119761897.
Installation finished successfully.
Sit back and relax and let the replication go….
Testing the Migration
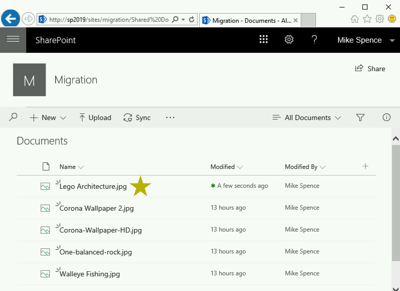
On the SharePoint 2019 team site a few images have been uploaded to the library:

Launch in a “Testing Mode”
We will now launch the VMs in a CloudEndure “Testing Mode”. Be sure to check the “Blueprint” settings for the machine that you are about to launch. There are a few things like subnet placement and instance type that I tweaked.
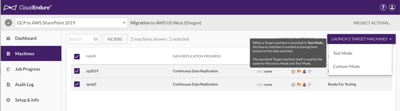
The machines went through a conversion process and the instances started on the AWS side according to the CloudEndure “blueprint” settings.

Now that we have these running on the AWS side we need to make sure we are testing the right machines because the original machines are still up and running. A little tricky with Windows domain joined machines. We will use local host file entries to point to the testing machines.
- Set a local host entry on the testing client to point to the test SharePoint host.
- Set a local host entry on the SharePoint host to point to the test SQL server host.
After setting these entries, I was able to access the SharePoint 2019 site and see my original content

Now going back to the original machines, be sure to check your DNS to make sure they are pointed to the original instances and remove any host entries you have added. From a CloudEndure perspective, the instances have now gone back to a “Continuous Data Replication” mode.

Enough testing already…Let’s Cutover!
I will go ahead and upload an additional image into the SharePoint library just to make sure when we cutover that I see the same content.
CloudEndure suggests stopping all operational services on the Source machines before cutover. For these instances, I will stop both SharePoint and SQL to make sure we are not updating any content during the cutover window.
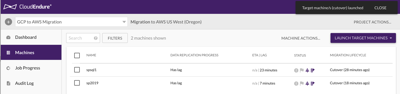
We are now looking at the CloudEndure console to make sure the “Lag” is “none” and ready to start our cutover. Basically the same process as testing occurs with a machine conversion and then startup of our target instance. One thing you should pay attention to are the security groups created on the AWS side. If I do this again, I would pre-create the required security groups and assign them in the source blueprints.
From the CloudEndure console, the source machines now show in a “Cutover” state. At this point, I shut down the instances in the GCP console although I haven’t deleted them yet.
After logging into the migrated instances, I verified basic SQL functionality. I notic
ed the following error after trying to connect with SQL Management Studio.

I’m sure this is some artifact of the migration process but a simple restart of the SQL service cleared the error.
Migration Success!
From my test client, I pulled up the SharePoint site and see the content that I updated earlier.

There were a few services leftover from the Google Compute Engine. Just as a feature request, it might be good to document those or remove them altogether during the conversion process. This is a very basic example and obviously there are much more complicated SharePoint environments that would require a good deal more planning.
My goal was just to gain a basic understanding of the CloudEndure migration process and learn a little GCP along the way. Hope this was helpful. Cloud On!
“The Cloud is an architect’s dream. Prior to the cloud if I screwed something up there was tangible evidence that had to be destroyed. Now it’s just a blip in the bill.” – Michael Spence
