In my latest Hands On series, I take a look at Parallels RAS version 17.1 deployed on AWS infrastructure. I have been following this product since the acquision of 2X (which you will still find references to scattered in some of the executables) by Parallels.

For a good portion of my career, I focused on the best way to get clients into the data center. Why? Because that is where all the applications and data lived. You needed good solid network solutions to get users access to those applications and data.
Along come the major SaaS players like Office 365, Salesforce, etc and many of the things I needed to get inside the data center for are now outside. Clients have less of a need to access the data center but need solid access to SaaS services. My arrows have flipped.
Life would be grand with clients just needing internet service, but as it turns out there are those pesky applications that just seem to refuse to move. Often these applications are some of the most mission critical to the enterprise. Now I have less of a need to get into the data center but I can’t eliminate it completely. That’s where Parallels RAS (Remote Application Server) steps into the picture.
Parallels RAS has a ton of features relating to access to remote PCs and VDIs, but for my purposes access to Microsoft RDS hosts is what I’m going to concentrate on and highlight just a few of the features of this product.
- Deployment Architecutre
- Software Installation
- RAS Publishing Server
- RAS Gateway Installation
- RAS Multi-Factor Authentication
- RAS SAML SSO to Azure AD
- RAS RDS Session Hosts
Deployment Architecture
Parallels RAS will run in Azure, AWS, or on-premises, you just need some Windows servers. For my purposes, I’m using AWS to deploy the architecture below all running on Windows Server 2019.
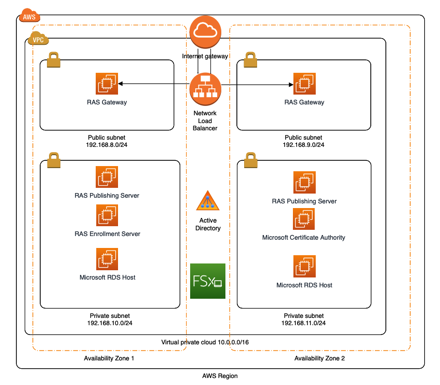
The main components consist of these servers:
- RAS Publishing Servers – I call it “RAS Central”. this where applications are published from and the configuration of RAS is performed.
- RAS Gateways – These are the servers that accept incoming client connections from the outside world.
- RAS Enrollment Server – This server interacts with a Microsoft Certificate Authority for certificates issued to clients involved with SSO.
- Microsoft RDS Hosts – These are where the applications actually run from.
- Active Directory – GPOs deployed to the Parallels RAS servers and RDS Hosts.
- FSx – AWS managed file system for user profiles from RDS hosts.
I’ll try and highlight some of the main features used in this deployment to hopefully get you up and running quickly with Parallels RAS. While they have some pre-built configurations you can use for your POC, I always believe “Hands On” is the best way to learn and understand the individual components.
One of the first things that you will run into with AWS is that you are going to need to open some ports between the various RAS and RDS servers. I put all of these into a single security group that is applied to servers in the RAS architecture. There is complete port listing in the RAS documentation and it is possible to separate out all the different pieces into a separate security groups, but for simplicity sake I’ve put them all in one SG applied across all the server. The YAML file is linked below that run can run inside of CloudFormation: ras-sgs-global.yaml
Software Installation
Now we can start building some servers. Parallels has a 30-day trial available that you can test out on your own. I basically built the environment in this order:
- RAS Publishing Servers
- RAS Gateways
- RAS Enrollment Server
- RAS RDS Hosts
RAS Publishing Server
Starting with the Publishing Server, install only the RAS Publishing Agent and the SSO component.
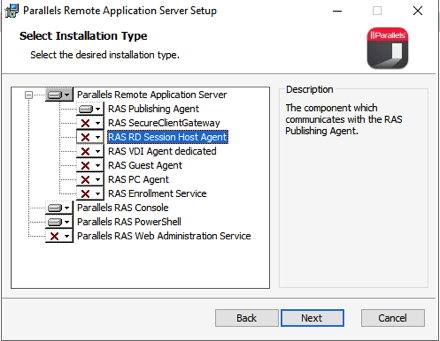
Reboot after the installs are finished and you should be ready to start configuring your RAS farm.
From that point forward, you can install all the pieces of the architecture directly from the Publishing Server without logging into any of the other nodes.
A recently added option in this version allows to force client upgrades before access to the RAS farm. It was a good thing since I really didn’t know my Mac client was way out of date.
There are a ton of options inside of the UI.
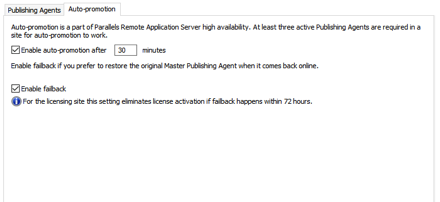
I’m always thinking a “disaster indifference” and thinking about high availability. Parallels RAS has some of these options already built into the product. Since the Publishing server plays such a crucial role, you can create multiple publishing servers in a Master/Secondary arrangement.
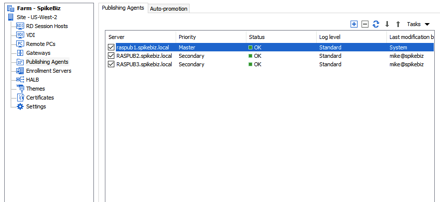
At that point, you can enable “Auto-Promotion” for the publishing role.
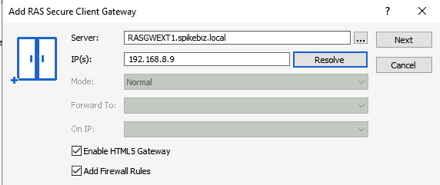
RAS Gateway Installation
The RAS Gateways are the brokers to our publishing servers and the backend published applications. They will take our SSL connections from the outside world. They will be integrated into an AWS Network Load Balancer (NLB) for high-availability. We will also enable the HTML5 support in these gateways as well. The security group(s) applied to these servers will need to allow HTTPS connections to the gateway servers from whatever range of addresses that you wish to allow.
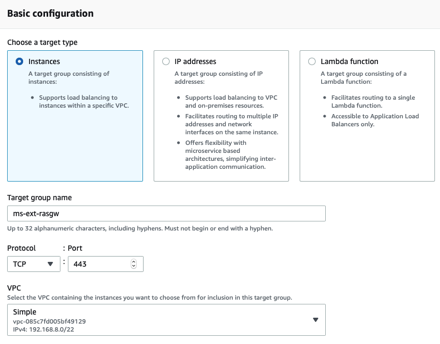
First create your AWS target group that will listen on TCP/443
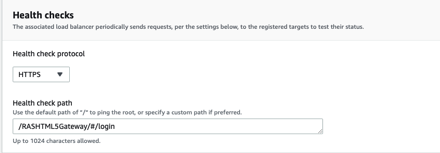
Pay particular attention to the health checks configured for the RAS gateway targets.
RAS Multi-Factor Authentication
Now that there are some gateways and an externally accessible load-balancer, we need to make provisio
ns for Multi-Factor authentication. In previous releases the choices were fairly limited to just Radius, but RAS now has a slew of built-in options.
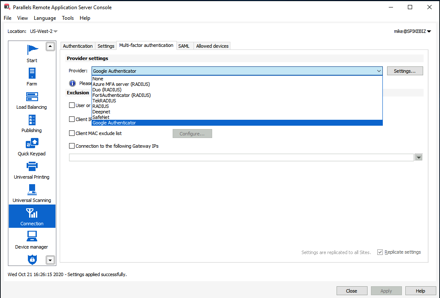
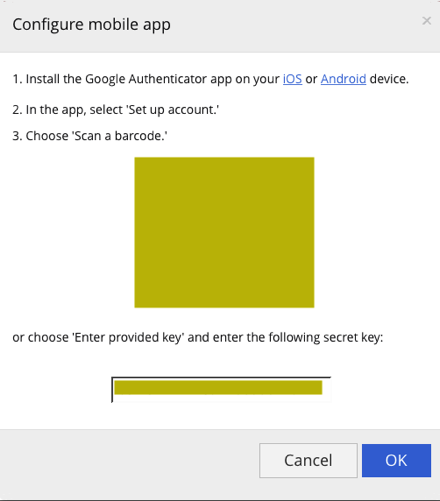
In a previous post I demonstrated how you use UDP load-balancing to load-balance Azure MFA on AWS. For the purposes of this post, I will use Google Authenticator. One first access via web-browser, I was prompted to setup MFA.
RAS SAML SSO to Azure AD
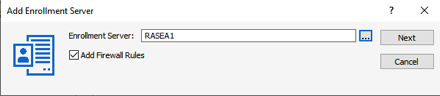
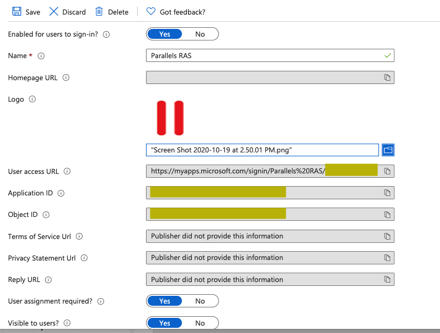
A fairly recent addition to the Parallels RAS configuration is the option to integrate with Azure Active Directory via SAML. As long as you have a functional Microsoft PKI in your environment, the setup is fairly straightforward. The steps for Azure AD are documented in this KB article: kb.parallels.com/en/124815 The prerequisities include a couple of AD accounts, some new certificate templates, and some permissions delegation. We also need a new RAS enrollment server.
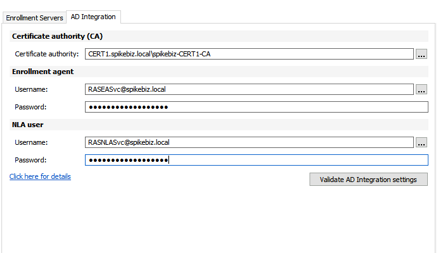
We then fill in the required information in the AD Integration fields.
We will start the configuration from Azure AD by creating a new non-gallery application and create the SAML Signing certificate.
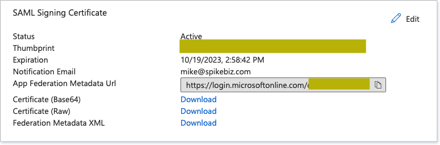
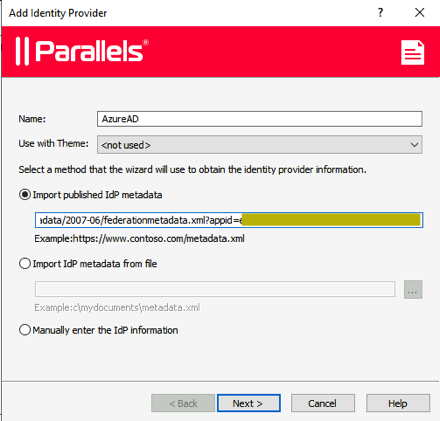
We now take the IdP metadata URL and add the Azure AD identity provider into RAS.
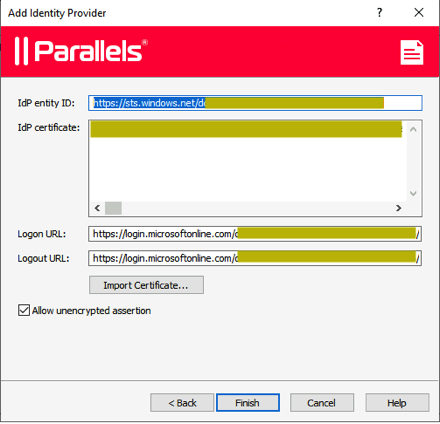
We then populate the SP (Service Provider) portion within RAS.
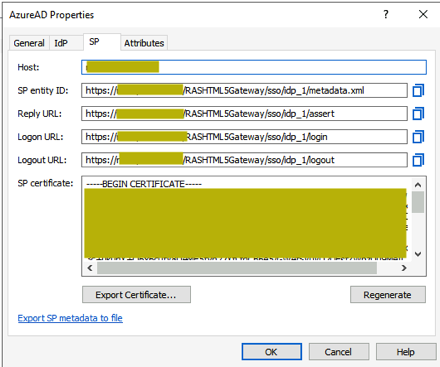
We take those values and plug them back into our Azure AD application configuration:
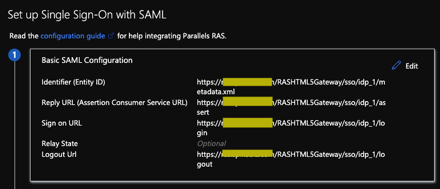
If all is well, we now have a Parallels RAS application within Azure AD

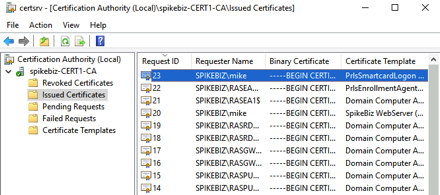
After a successful logon, check your CA to see if the new certificate templates have been used to issue the RAS related certificates.
RDS Session Hosts
Now that we have the basics of the RAS farm configured, we are ready to publish some applications on RDS Session Hosts. We want high-availability for our hosts and users should have a consistent experience regardless of which host they access.
A combination of group policy and a user file share will be used to help provide that consistency. Although you can use most any file share, I prefer to use Amazon FSx as a managed file service (one less thing for me to manage).
The initial setup is well documented in the AWS FSx Documentation. Once you have your FSx file system up and running, you can create a user share for the RDS session hosts. With a couple of powershell commands, you will be up and running.
PS> enter-pssession -ComputerName <ps-endpoint>.spikebiz.local -ConfigurationName FsxRemoteAdmin
PS> New-FSxSmbShare -Name “Users” -Path “D:\Users” -Description “User Profiles” -FolderEnumerationMode AccessBased -ContinuouslyAvailable $True -EncryptData $true
PS> grant-fsxsmbshareaccess -Name “Users” -AccountName Everyone -AccessRight Full
Since the AWS FSx names can be a little cryptic, I use DFS to point to them with a more friendly name.
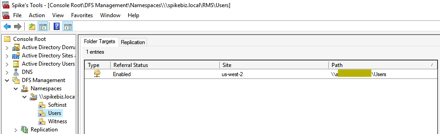
I will then use this share inside of the RDS GPO to redirect users profiles.
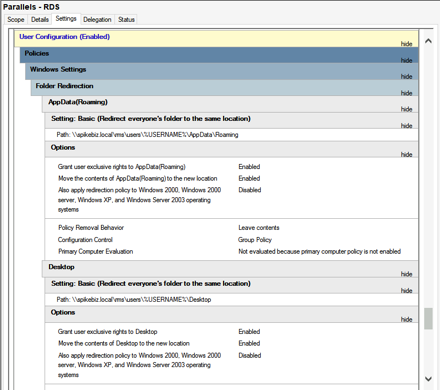

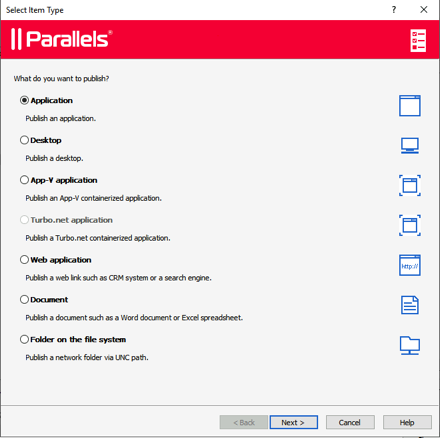
We can now install some applications to publish from the RDS hosts. If it will run on a RDS host, then you can publish it. You can publish all sorts of items from RAS
In my testing environment, I published a few applications including Office, RoyalTS to manage servers, and a software file share. I prefer to use the Parallels client but you can just as easily use the HTML5 interface that we launch from our Azure AD application (SAML SSO).
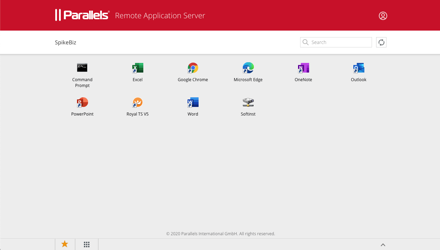

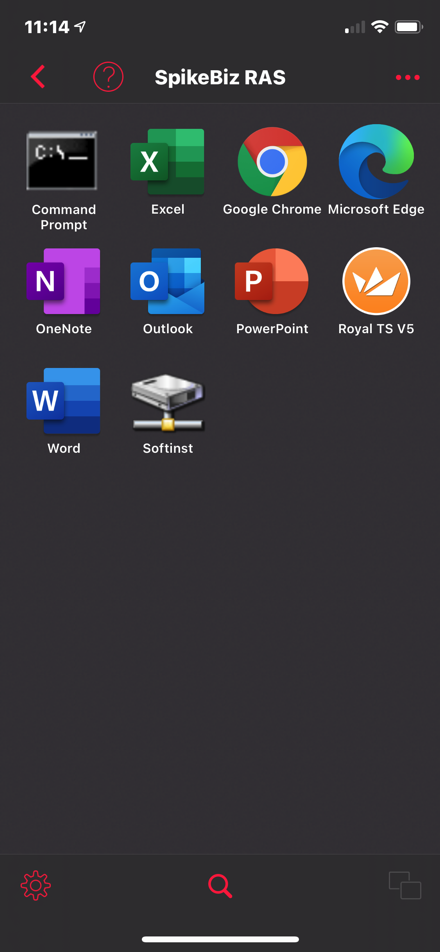
I now get a consistent set of applications across all sorts of platforms and I can do all sorts of strange things like:
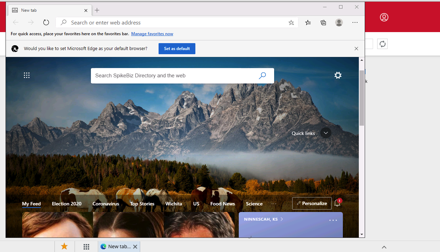
Running Edge inside of Chrome:
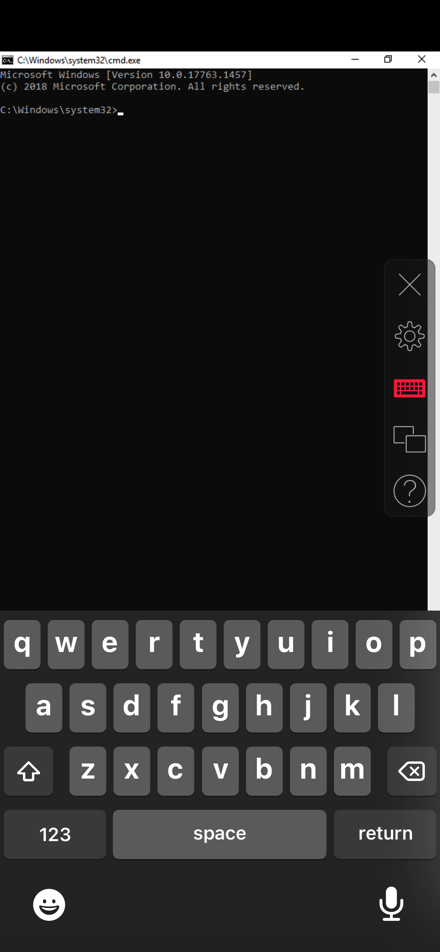
Running a Command Prompt on your iPhone:
Summary
Parallels RAS is a solid product for application delivery. If you’ve reached the point where data center and intranet access is dwindling, then I would give Parallels RAS a try. It is packed full a features and whether you are supporting domain-joined machines, COPE, or BYOD, Parallels RAS can make them work.
Cloud On!
The cloud is an architect’s dream. Prior to the cloud if I screwed something up there was tangible evidence that had to be destroyed. Now it’s just a blip in the bill. – Mike Spence
